1
ITEC 610 PROJECT DESCRIPTIONS
(If you download this file, use Ctrl+Click on the links below to access the specific project.)
INDIVIDUAL PROJECTS
I-1: Enterprise Architecture Plan (Page 3)
I-2: Technology Management Plan (Page 10)
I-3: Technology Innovation Project (Page 17)
GROUP PROJECTS
G-1: Infrastructure Modernization Review (Page 24)
G-2: IT Security Risk Assessment (Page 30)
G-3: Health Information Technology Architecture (Page 38)
2
Individual Projects
3
Individual Project I-1
1. Title
Enterprise Architecture Plan
2. Introduction
Largo Corporation is a major multinational conglomerate corporation which specializes in a wide array
of products and services. These products and services include healthcare, finance, retail, government
services, and many more. The annual revenue is about $750 million and it has about 1,000 employees.
The parent company is headquartered in Largo, Maryland and its subsidiaries are located throughout
the United States.
The mission of the corporation is to bring the best products and services to people and businesses
throughout the world so they can then realize their full potential.
The corporate vision guides every aspect of their business to achieve sustainable, quality growth:
• Productivity: Be a highly effective, lean and fast-moving organization.
• People: Be a great place to work where people are inspired to achieve their maximum potential.
• Partners: Nurture a winning network of customers and suppliers, together we create mutual,
enduring value.
• Responsible: Be a responsible citizen that makes a difference through ethical behavior.
• Revenue: Maximize long-term return while being mindful of our overall responsibilities.
The company’s culture is reflected in their corporate values:
• Leadership: Courage to shape a better future.
• Collaboration: Leverage collective intelligence.
• Accountability: Own up to your responsibility.
• Passion: Committed to excellence.
• Diversity: Provide new perspectives into our business.
• Quality: We will want quality as part of our brand.
The corporation consists of the parent company and the following subsidiaries:
• Healthcare – Suburban Independent Clinic, Inc. (medical services)
• Finance – Largo Capital (financial services)
• Retail – Rustic Americana (arts and crafts), Super-Mart (office products)
• Government Services – Government Security Consultants (information security)
• Automotive – New Breed (electric cars)
• Systems Integration – Solutions Delivery, Inc. (communications)
4
• Media Design – Largo Media (website and app design)
The organization is headed by CEO Tara Johnson who completed her Master’s degree at UMUC and
eager to make worthwhile improvements to the corporation. She rose through the ranks of Largo
Corporation starting with systems integration, then retail and her last position before becoming CEO
was in finance.
The corporation is in a highly competitive environment so the CEO wants savvy employees at many
levels to make wise judgments and take an aggressive approach and deliver results towards improving
the bottom line yet maintaining corporate social responsibility.
Corporate Issues
Ms. Johnson is aware of the many enterprise wide problems Largo Corporation and its subsidiaries are
facing which include:
• The complexity of IT is constantly increasing
• Many disparate systems do not interoperate among the parent company and the subsidiaries
and among the business units
• Many duplicate systems across different business units which perform the same function
• Each part of the organization has their own unique technology standards
• It is a major challenge to integrate technology into the daily operations of the organization
Because of these problems, IT systems in the corporation often failed to meet organizational goals and
objectives.
A Potential Solution
A few months ago, Ms. Johnson attended a symposium for CEOs and other senior executives and
learned about enterprise architecture and how it can enable business-IT alignment and agility. Upon her
return, she floated the idea with the board of directors, her direct reports and vetted the idea with IT
Operations head Mr. Sculley. With strong support from the board and Mr. Sculley, Ms. Johnson created
an enterprise architect position reporting directly to her with dotted line reporting to all area heads.
You have been handpicked to serve as the new Chief Enterprise Architect for Largo Corporation. Your
assignment is to craft an enterprise architecture vision and explain how the vision enables business
goals. Among other things, you need to justify the implementation of an enterprise architecture at
Largo Corporation.
According to the U.S. Government Accountability Office, “an enterprise architecture (EA) is an integral
part of the IT investment management process. An EA provides a clear and comprehensive picture of
the structure of an entity. This picture consists of snapshots of its current and proposed technical
environments, and a roadmap for transitioning from the current to the target environment. When
properly managed, an EA can help optimize the relationships among an organization’s business
operations and the IT infrastructure and applications supporting them.”
5
You will learn about the EA concept, various EA frameworks and apply one to the Largo Corporation. You
will learn how to migrate the corporation to a well-defined enterprise architecture vision. As part of the
migration effort you will need to identify the governance structure for the architecture.
As an enterprise architect, your ability to understand and apply enterprise architecture principles and
methodology enables the organization to achieve a business-IT aligned, agile and scalable IT asset. This
in turn enables the organization to leverage IT as a competitive strategy to respond quickly to changing
market conditions in a global economy. Additionally, you must be able to communicate effectively (oral
and written) to executive level management in a non-jargon, executive level manner. This learning
demonstration is designed to strengthen these essential knowledge, skills, and abilities needed by
enterprise architects.
3. Steps to Completion
1) Understand the Enterprise Architecture Concept
You need to first understand the foundational concepts of an EA including what it is and why it is
needed. Conduct research to gain an understanding of the concept and determine how it might apply to
Largo Corporation.
An informative reference book is “An Introduction to Enterprise Architecture: Third Edition” by Scott A.
Bernard (start at Pg. 29).
https://books.google.com/books?id=OkNMFI3_L_YC&printsec=frontcover&dq=enterprise+architecture
&hl=en&sa=X&ei=WttEVc7mOoWhNsSMgMgG&ved=0CDkQ6AEwAQ#v=onepage&q=enterprise%20arch
itecture&f=false
The role of an enterprise architect is captured well in this article:
https://www.cio.com/article/2438311/enterprise-architecture/enterprise-architect.html
Deliverable: Prepare an interim report for corporate executives explaining the enterprise architecture
concept and discuss its applicability to Largo Corporation. Minimum 400 words and include at least 3
references. (An interim report will be consolidated to a final deliverable in a later step.)
2) Review EA Frameworks
Research various enterprise architecture frameworks. Examples include The Open Group Architecture
Framework (TOGAF), the Federal Enterprise Architecture (FEA), and the Zachman Framework. Compare
and contrast these frameworks. A good starting point is this article by Roger Sessions:
http://www3.cis.gsu.edu/dtruex/courses/CIS8090/2013Articles/A%20Comparison%20of%20the%20Top
%20Four%20Enterprise-Architecture%20Methodologies.html
A variety of frameworks are also mentioned in this source (parting on Page 11):
https://books.google.com/books?id=Fs5bMNBXLEMC&printsec=frontcover&dq=enterprise+architecture
6
+frameworks&hl=en&sa=X&ei=fdxEVZ32HYqXNtitgXg&ved=0CDYQ6AEwAQ#v=onepage&q=enterprise%
20architecture%20frameworks&f=false
Deliverable: Compare and contrast at four different major architectural frameworks based on various
attributes and report your findings in a summary table. Include brief descriptions and sources of your
information. Include at least 3 references.
3) Understand the TOGAF Framework
For this project we will use the TODAF architectural framework described starting at the Introduction
(http://pubs.opengroup.org/architecture/togaf9-doc/arch/chap01.html). Use the “Next>>>” link (upper
right hand corner and lower right hand corner) to advance to the next topic “Core Concepts.” Explore
this resource.
Next read “TOGAF as an Enterprise Architecture Framework”:
http://pubs.opengroup.org/architecture/togaf8-doc/arch/chap02.html
4) Execute the preliminary phase of the architecture development process.
Start by reviewing the Architecture Development Method (ADM) beginning at:
(http://pubs.opengroup.org/architecture/togaf8-doc/arch/chap03.html)
Walk through the Preliminary Phase (http://pubs.opengroup.org/architecture/togaf8-
doc/arch/chap04.html).
Deliverables for this step include: (a) Define the architectural framework in the form of a diagram
specific to Largo. (b) Identify at architectural principles you feel are applicable to Largo Corporation. (c)
Create the future vision diagram for the company. Details on each deliverable are defined below.
(a) The framework diagram needs to be organization-specific. This architecture vision should
take into account the “corporate issues” identified in the Introduction of this learning activity.
You are free to make assumptions and hypothetical scenarios behind your architectural vision.
Examples of frameworks can be found at: http://pubs.opengroup.org/architecture/togaf8-
doc/arch/chap37.html
(b) Provide architecture principles for the following domains: business, data, application, and
technology for Largo Corporation. Examples can be found at:
http://pubs.opengroup.org/architecture/togaf8-doc/arch/chap29.html#tag_30_06
Your principles should try to address the problems identified in the Introduction section of this
learning activity.
Identify at least 3 principles for each domain and explain its applicability to Largo Corporation.
7
To document your principles, you may use the template at:
https://www2.opengroup.org/ogsys/jsp/publications/PublicationDetails.jsp?catalogno=i
093 (You will need to set up an account if you have not previously). Download the zip
file and open: TOGAF_9_Templates > Deliverables > Architecture Principles and open
the Word document.
(c) To define the future vision, you can create a solution concept or a value chain diagram. This
is an important step that articulates your perspective of the future architecture of Largo
Corporation. Include an explanation for your vision including why it is appropriate for the
company.
Templates that you may use are downloadable from:
https://www2.opengroup.org/ogsys/jsp/publications/PublicationDetails.jsp?catalogno=i093
(You will need to set up an account). Download the zip file and open: TOGAF_9_Templates >
Artifacts > Core Diagrams > Architecture Vision and open the two PowerPoint presentations.
5) Prepare a Migration Plan
Research migration planning resources such as: http://pubs.opengroup.org/architecture/togaf8-
doc/arch/chap12.html
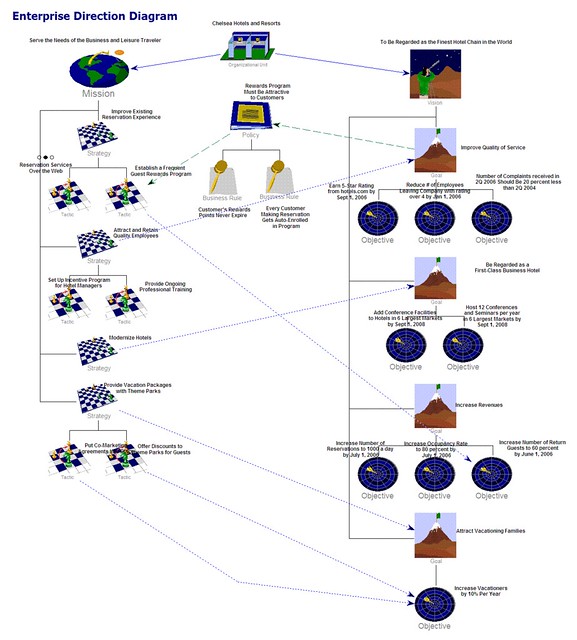
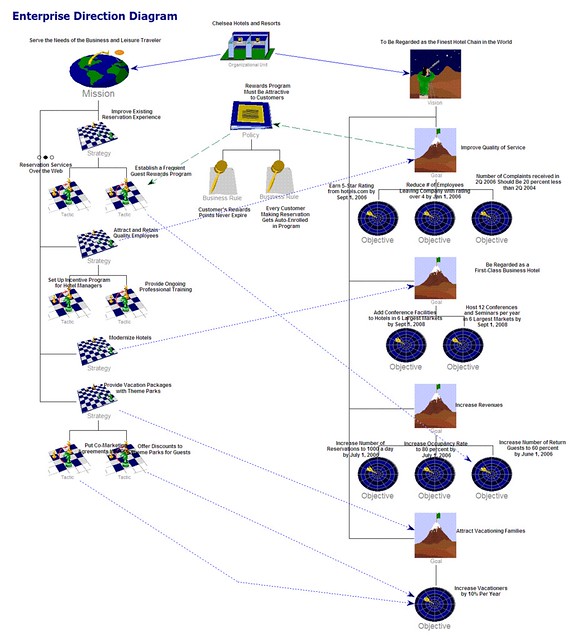
Another way to articulate the migration plan is through an Enterprise Direction Diagram – an example is
shown at:
Another example is Slide 23 in this slide presentation:
https://www.slideshare.net/wintonjkt/enterprise-architecture-for-dummies-togaf-9-enterprisearchitecture-overview
Deliverable: Outline a plan and include an Enterprise Direction Diagram or similar graphic to address
migrating to the target architecture as defined in the architectural vision. In other words, this plan
should address how the organization will move from the “as-is” to the “to-be” state.
Minimum length is 400 words.
6) Define the Architecture Governance Process and Structure
Architecture governance is defined as the set of activities an organization uses to manage and control its
enterprise architectures and other architectures. This process institutionalizes decision making and
ensures accountability. More at: http://pubs.opengroup.org/architecture/togaf8-doc/arch/chap26.html
8
Research this topic and for the Largo Corporation enterprise architecture, define the “who”, “what” and
“where” associated with this process. For example, who is responsible for governance (e.g., establish an
architectural governance board?), what will be managed and controlled and where in the organization
will controls be applied.
Deliverable: Summarize your findings in an interim architectural governance document. Minimum
length is 400 words.
7) Communicate the Architectural Vision.
The final deliverable is a narrated PowerPoint presentation that summarizes all of the key findings and
recommendations from the previous steps. The target audience is the CEO and other executives in the
organization. Be sure to address the following information:
– Introduction – Describe the issues facing the corporation then define an enterprise architecture
and explain why it is needed for Largo Corporation. Provide a short summary of the architectural
frameworks and explain why TOGAF is applicable to Largo Corporation. (From Steps 1, 2)
– Architecture Vision: Describe the architectural framework, architectural principles and future
vision specific to the corporation. (From Step 4)
– Migration Plan: Outline the steps needed to transition from the current state to the desired state
(From Step 5)
– Architectural governance structure: Provide highlights from the architectural governance
document. (From Step 6)
The presentation should consist of 10-15 slides. It should include audio narration (directions are found
at: https://support.office.com/en-au/article/Add-narration-to-a-presentation-0b9502c6-5f6c-40aeb1e7-e47d8741161c). The narration should also be captured in the slide notes.
4. Deliverables
1) Interim Report on the EA concept
2) Summary matrix on architectural frameworks
3) Architectural framework for Largo Corporation
4) Architectural principles
5) Future vision diagram
6) Migration plan
7) Architecture governance process and structure
8) Architectural vision final presentation
Except for the presentation, combine all of the files into one Word document. Provide an abstract,
introduction, table of contents and conclusion in this one document.
9
Title your files using this protocol: LastName_FirstName_I-1_AssignmentName_Date.
In lieu of submitting the presentation, you may provide a link to your presentation file.
5. Rubrics
Criteria Weight Score
Define the enterprise architecture concept and identify key architectural
frameworks used in practice
20
Formulate an architectural framework for a given organization and
identify applicable architectural principles relevant for that organization
20
Design and develop an enterprise architecture vision that
accommodates components of the enterprise
30
Create a migration strategy in transforming an enterprise architecture 10
Evaluate the role of architectural governance in managing enterprise
systems
10
Exhibit communication skills 10
Total 100
10
Individual Project I-2
1. Title
Technology Management Plan
2. Introduction
You have been selected to be the acting CIO for a subsidiary of Largo Corporation called Rustic
Americana. Its primary products include arts and crafts that reflect the history, geography, folklore and
cultural heritage of the United States. It specializes in direct marketing and sales through its call center.
Sales are through a web store, a brick and mortar store, and a direct mail catalogue. All services are
housed under one roof that include warehousing, order fulfillment, shipping, corporate management
and operations, and the call center. The success of the company hinges on its eye-catching direct mail
catalogue and the unique product line.
Unfortunately, annual sales have declined over the years due largely due to internal issues. The previous
CIO was terminated some say due to incompetence primarily related to the underperforming call center.
In addition, speculation swirled around the activities of the CIO. He was often absent from the building.
He secluded himself behind the closed door of his office. Associated rumors mounted, and it was
believed that he was running a consulting business on company time. When the Rustic Americana CEO
asked him about this during a formal review, the CIO answered that it was a weekend hobby that kept
him abreast of emerging technologies. The CEO asked him if one of their competitors was a client and he
vehemently denied the accusation. She was certain that the CIO was not being entirely truthful with her.
Call Center Operations
Managing a call center demands a wide range of skills including managerial, troubleshooting, patience
and being cool under pressure. Knowledge of computer and communications skills is helpful but most
call centers have a technical support division. The call center manager is Prisha Khan – she has been in
the job for about 2 months.
The customer service representative (CSR) in the call center responds to a call for product. On the
customer management system (CMS), the CSR collects and directly enters customer information; on a
separate inventory management system (IMS), the CSR looks up the product, and verifies if the
warehouse has it in stock. If it does, the order is entered on the CMS, and the CSR decreases the
inventory on the IMS. On the CMS, the CSR creates an order fulfillment ticket that is automatically
shuttled to the warehouse processing clerk who prints it and then generates the shipping label. The
shipping label is prepared through a web-based system through either UPS or USPS, which also produces
a tracking number used by both the company and the customer. The processing clerk enters the
shipping costs and tracking number into the CMS. The customer is billed when the order ships.
The warehouse crew uses bar code scanners to track merchandise; once the order is selected, it moves
along a conveyor to a shipping clerk who packages the order, affixes the shipping label, scans the bar
11
code, and places the package into a bin for delivery pick-up. The final scan automatically enters the
dollar amounts into the system for billing.
An old UNIX system is used to manage inventory. Data input clerks entered information on new
merchandise into it, CSRs referred to it for product data, and if the product was on hand, it produced an
order processing form which was sent to the warehouse for processing. The CSR could reduce the
inventory through the terminal on their desk. The problem they experienced was a refresh rate on
volatile inventory. It was a common occurrence that a customer would be told the product would ship
when it was in fact depleted by other CSRs.
There were conflicting views on the party responsible for upgrading the systems. The former CIO
believed the call center manager needed to take the lead on upgrading operations, while the call center
manager complained that this was an IT problem and she could not tolerate downtime. To add to the
fray, the Chief Financial Officer balked at the cost associated with this investment. The CEO did not feel
the urgency and leaned to the CFO for advice.
Staffing the call center is the responsibility of the call center manager. Ms. Khan uses past volume
experience to make sure there were sufficient CSRs on hand. She kept a list of “on-call” CSRs for
unanticipated business. Her staffing limit was the number of stations with computer access to the
servers. The call center uses a Cisco Voice over Internet Protocol (VoIP) phone system. The phone
system runs on two standalone servers — one for call routing and the other for voicemail. There is a
dedicated toll free number into the center, and the system is programmed with an auto-attendant to
direct calls. The volume of calls is a problem, and the number of lines is less than the number of agents
available to take calls during high volume periods. This is because there is a per-trunk monthly service
charge and the call center cannot adjust the number of trunks based on periodic demand. When the
caller is placed in queue, the standard practice is to limit the length of the average call to six rings. The
phone system requires a local coaxial cable Internet service to supply broadband. Phones are connected
to the network architecture using standard Cat5 copper cabling which routes phone traffic to the call
center.
Under this approach, there have been issues with “quality of service.” The former CIO was fond of
saying “problems with the cable company” when things went wrong. There was no effort to track
downtime. During these “downtimes” the entire call center becomes idle and revenue is lost. Because
the Internet is tied to the same cable service, web services were also down. The Rustic Americana CEO
felt that the lack of access discouraged new customers, but no data was collected to indicate a
correlation between downtimes and sales decline.
Inside the building there is an application server, a server for Microsoft Outlook email, the web server,
and the typical complement of routers and switches. The former CIO used a variety of hardware from
different vendors. When broadband cable services are up, bandwidth is not a problem, except when the
former CIO allowed employees to stream movies during their breaks to boost morale. Employees
routinely used their workstations to check personal email, and to manage their social networking
12
accounts. There was a problem with one employee posting unflattering comments about the company
that resulted in a severe reprimand.
The data systems for the call center are setup as follows. The center has two data servers. One data
server has a UNIX operating system, and it runs Oracle database technology. The second server is a
Microsoft operating system, and it runs SQL database technology. The two data servers are accessed via
40 workstations in the call center. It is staffed 24/7 but is closed on major holidays. The call center also
contains 10 additional older workstations, which are used by data input clerks to update inventory when
ordered and upon arrival this inventory was verified and bar code tagged with local stock inventory
labels.
CSRs use a “homegrown” customer support application developed in house which uses a generic Oracle
Forms interface. The former CIO did not believe in “bells and whistles” of modern Customer Resource
Management (CRM) systems — besides, the Director of Marketing did not understand the value of CRM,
the CFO was not persuaded to make the software and hardware investments, and the Rustic Americana
CEO held stereotypical, non-strategic views of customers. The inability to do their required work was a
constant complaint of agents. Moreover, there is no technology infrastructure in place to support
mobile computing such as staff use of tablets or (more critical) a wireless interface on bar code scanners
used in the warehouse.
Your Role as Acting CIO
You should frame your work around understanding the mechanics of enterprise technology
management beyond the need to specifically recommend the replacement of antiquated yet functional
systems. You should strive for an alignment of technology with the business needs.
You have been asked by the Corporate CEO to fix the problems created by the former CIO’s perceived
mismanagement of the IT operations and resources. In particular, you need to address the numerous
complaints about the call center regarding its poor service such as delayed shipping and failure to notify
when a product is out of stock.
The CEO asked that a plan be prepared and presented for effectively managing the company’s IT
operations – specifically its call center. Within Rustic Americana, there is a Chief Financial Officer, a
Director of Marketing, a Direct Sales Director and the usual departments. You are the “acting” CIO, and
as such, you have your own staff of ten which includes an assistant who handles staff management and
equipment orders, a network engineer for each of the three critical systems, a systems analyst, a web
server programmer, and four desktop support technicians.
This learning activity focuses what it takes to manage technical operations. You will learn about creating
reliable feedback mechanisms for difficulties at all levels of enterprise Information Technology interface.
This includes timely discovery of technology related issues, resolution of these issues, creating a culture
of trust and dependence, informing staff of your activities, and developing strategic plans for reducing
bottlenecks in the future.
13
Understanding technology management is important to an IT professional because in this environment,
as would be true of most corporate environments, computer-based information systems are at the core
of an efficient and competitive service delivery. Effective leadership requires the identification of
problems, the resolution of those problems, an eye on the future of the corporation and its profit, and
transparency through communication with peers and subordinates.
3. Steps to Completion
1) Analyze the Situation
First review and analyze the business and IT operations of the call center. Break down the entire
process into smaller parts and analyze these parts. If necessary draw a sketch.
In general, here are some typical questions one should consider as part of the analysis:
1. What is the business model for the corporation?
2. Where is technology strong? Where is it weak?
3. How do we manage capacity both in terms of our computer system’s capacity (and response
time and fault tolerance) and our staffing capacity (does the work performed full occupy the
expertise for which it is paid?).
4. What is our sustainability policy?
5. What is our technology innovation strategy?
6. What is our level of contract support? How are contracts evaluated for their full value to the
efficiency of the corporation?
7. How are problems solved within the corporation?
Next identify key issues and challenges. Beyond technical concerns, there are also managerial issues
that need to be addressed.
Deliverable: Capture this information in an issue matrix which is a table that lists, categorizes and
prioritizes these problems (High, Medium, and Low), that assigns responsibility for the problem to
internal staff, to contract support, or to others (specify these individuals) and contain other information
you feel relevant. This will be shown to management so they will readily identify and understand the
key concerns. Use your creativity.
Identify problems and do not jump the gun and start identifying or implying solutions at this point.
Solutions are to be presented in Step 3.
14
2) Identify Best Practices
Research current best practices relating to technology management practices including operational
improvement approaches. You can start with these U.S. Government Accountability Office (GAO)
information:
• Managing Technology: Best Practices Can Improve Performance and Produce Results
http://www.gpo.gov/fdsys/pkg/GAOREPORTS-T-AIMD-97-38/pdf/GAOREPORTS-T-AIMD-97-
38.pdf
• Information Technology: Implementing Best Practices and Reform Initiatives Can Help Improve
the Management of Investments http://www.gao.gov/assets/670/663051.pdf
Also, key management best practices are listed in Chapter 2 of this reference:
https://books.google.com/books?id=SPjRBQAAQBAJ&printsec=frontcover&source=gbs_ge_summary_r
&cad=0#v=onepage&q&f=false
(Note: If you have trouble accessing this reference, you will need to go to the Safari e-book database. To
do this, go to the library home page at http://www.umuc.edu/library, click Databases by Title (A-Z ), and
then S, and then the Safari Books Online database. Using the search bar, you can then locate the book
entitled “IT Best Practices”. Click on the book that is by Tom C. Witt. Proceed to Chapter 2.)
Also identify people management skills needed to have an effective operation. You can begin with this
link: http://www.forbes.com/sites/victorlipman/2014/06/09/6-tips-for-managing-people-who-are-hardto-manage/
Understand ethical requirements for individuals in an organization. Here is a Prezi presentation about
the subject:
https://prezi.com/swchhg04exdh/how-ethical-theories-apply-to-it-professionals/
Deliverable: Prepare a best practices report that addresses the key findings from this step. This will be
shown to corporate management. Minimum length: 400 words.
3) Select Applicable Operational Improvements
You are to identify what is needed for managing the call center. You use all of your staff as a team to
identify solutions (Note: you may request for new positions on your staff but you cannot exceed your
current number of slots).
You have a sense of the problems; now document the best practices which, if implemented, generate a
computing environment more stable, reliable and innovative and help in resolving the challenges you
have set as top priorities facing your corporation.
15
Specifically, identify needed operational improvements applicable to Rustic Americana’s call center with
a set of recommendations. Among other approaches, explore the use of ITIL to provide customercentric IT services. Here is a good starting resource: https://docs.newhorizons.bg/itil/ITIL-the-basicsWhite-Paper.pdf
Here is an introduction to call centers:
https://books.google.com/books?id=0ZdG1qF2XvYC&printsec=frontcover&source=gbs_ge_summary_r&
cad=0#v=onepage&q&f=false
Also, be sure to address ethical behavior based on concerns raised in this learning demonstration. This
has been a major concern in Largo Corporation because of recent unethical corporate practices that has
been in the news recently.
Also address needs for the support, renewal, and sustainability of a call center technology. Be sure to
specify effective day-to-day practices needed to manage operations.
Deliverable: Develop an operational improvement report that summaries the key requirements
discussed above. Minimum length: 600 words.
4) Document Findings and Recommendations
Document key findings and recommendations in a presentation to your executive team (e.g., CEO, CFO,
and Director of Marketing). This presentation should document the issues and solutions identified
earlier.
Deliverable: Final presentation
The presentation should consist of 10-15 slides. It should include audio narration (directions are found
at: https://support.office.com/en-au/article/Add-narration-to-a-presentation-0b9502c6-5f6c-40aeb1e7-e47d8741161c). The narration should also be captured in the slide notes.
4. Deliverables
1) Issue matrix
2) Best practices report
3) Operational improvement report
4) Final presentation
Except for the presentation, combine all of the files into one Word document. Provide an abstract,
introduction, table of contents and conclusion in this one document.
Title your files using this protocol: LastName_FirstName_I-2_AssignmentName_Date.
In lieu of submitting the presentation, you may provide a link to your presentation file.
16
5. Rubrics
Criteria Weight
(%)
Score
Identify and analyze issues prevalent in a technical environment 20
Create a strategy for the management oversight of enterprise
technology resources including the IT infrastructure reflecting best
practices
30
Identify operational solutions to issues in a technical environment 30
Apply ethical principles when determining actions 10
Exhibit communication skills 10
Total 100
17
Individual Project I-3
1. Title
Technology Innovation Project
2. Introduction
Background of the Corporation
Largo Corporation is a major multinational conglomerate corporation which specializes in a wide array
of products and services. These products and services include healthcare, finance, retail, government
services, and many more. The annual revenue is about $750 million and it has about 1,000 employees.
The parent company is located in Largo, Maryland and its subsidiaries are headquartered throughout
the United States.
The mission of the corporation is to bring the best products and services to people and businesses
throughout the world so they can then realize their full potential.
The corporate vision guides every aspect of their business to achieve sustainable, quality growth:
• Productivity: Be a highly effective, lean and fast-moving organization.
• People: Be a great place to work where people are inspired to achieve their maximum potential.
• Partners: Nurture a winning network of customers and suppliers, together we create mutual,
enduring value.
• Responsible: Be a responsible citizen that makes a difference through ethical behavior.
• Revenue: Maximize long-term return while being mindful of our overall responsibilities.
The company’s culture is reflected in their corporate values:
• Leadership: Courage to shape a better future.
• Collaboration: Leverage collective intelligence.
• Accountability: Own up to your responsibility.
• Passion: Committed to excellence.
• Diversity: Provide new perspectives into our business.
• Quality: We will want quality as part of our brand.
The corporation consists of the parent company and the following subsidiaries:
• Healthcare – Suburban Independent Clinic, Inc. (medical services)
• Finance – Largo Capital (financial services)
18
• Retail – Rustic Americana (arts and crafts), Super-Mart (office products)
• Government Services – Government Security Consultants (information security)
• Automotive – New Breed (electric cars)
• Systems Integration – Solutions Delivery, Inc. (communications)
• Media Design – Largo Media (website and app design)
The organization is headed by CEO Tara Johnson who completed her Master’s degree at UMUC and
eager to make worthwhile improvements to the corporation. She rose through the ranks of Largo
Corporation starting with systems integration, then retail and her last position before becoming CEO
was in finance.
The corporation is in a highly competitive environment so the CEO wants savvy employees at many
levels to make wise judgments and take an aggressive approach and deliver results towards improving
the bottom line yet maintaining corporate social responsibility.
Corporate Issues
Ms. Johnson is very concerned about the outlook of her company. Revenues recently declined and she
felt that the organization needed a transformation for the company to do well over the long term. In
thumbing through some readings she was inspired when she uncovered the following:
We live in a business world accelerating at a dizzying speed and teeming with ruthless
competition. As most of the tangible advantages of the past have become commoditized,
creativity has become the currency of success. A 2010 study of 1,500 CEOs indicated that leaders
rank creativity as No. 1 leadership attribute needed for prosperity. It’s the one thing that can’t be
outsourced; the one thing that’s the lifeblood of sustainable competitive advantage.
Unfortunately, most companies fail to unleash their most valuable resources: human creativity,
imagination, and original thinking. They lack a systematic approach to building a culture of
innovation, and then wonder why they keep getting beaten to the punch. (Linkner, 2011)
She decided to establish a team responsible for defining an operational process that would result in
innovations that would both counter potential future threats as well as provide a competitive edge for
the corporation.
You have been chosen by the CEO as the “Innovation Team” leader. All members of the team need to
understand the process of environmental scanning in order to identify innovative technologies that
allow the corporation to respond to potential threats and dynamic changes in business and operational
requirements. Further, she has directed you to provide solutions robust enough to address unforeseen
market choices and demand. Hence, you should always allow for serendipitous discoveries, that is, ideas
that you stumble across which have potential future benefits which may not be immediately aligned
with the current mission.
19
This learning activity establishes your understanding of how innovation is accomplished in an
organizational environment. As you quickly discover, innovation hinges on providing an environment
that nurtures and values creativity and innovation. Fresh ideas often arise from solving problems
nagging the organization. Keep in mind that genius rarely resides in the head of one individual within the
organization. Yes, you have the “Steve Jobs” types of executives upon whose shoulders the vision rests
and without whom there is no vision. But this is rare. Equally rare will be the “hidden employee gem”
whose sudden inspiration saves the day.
You will understand the innovation life cycle process. It begins with ideation, that is, understanding the
problems through a review of purpose and structure. In a later stage, an example of a concept you will
learn as part of the innovation process is the “crowdsourcing” model that scours the Internet, creates
internal discursion opportunities, and creates strategic alliances with external partners (Brabham, 2013).
IT professionals need to understand the importance of innovation and how to achieve it in their
organization. Innovation is doing something different that has an impact on the business’ operations.
Innovations are not often on the leading edge of technology. They can be as simple as migrating
operations from one form of processing to another, switching to a greener lighting solution, outsourcing
desktop support, investing in a stronger email security system and so on. Most innovations result from
proactive thinking and what we will call a “corporate mindfulness”.
All IT professionals must be able to communicate effectively (oral and written) to executive level
management in a non-jargon, executive level manner that convincingly justifies the need to invest in IT
improvements and modernization. In addition, you will be developing critical thinking and key
leadership skills. This learning demonstration is designed to strengthen these essential knowledge, skills,
and abilities needed by IT professionals.
3. Steps to Completion
1) Perform Environmental Scanning
Environmental scanning involves identifying external opportunities and threats for an organization.
(a) Select one subsidiary of Largo Corporation. Research and project future potential threats to the
subsidiary.
(b) Also identify potential disruptive technologies that the subsidiary may leverage in order for it to
succeed in the future to counter future threats. As a start, here are several sources you might want to
check (in addition to your readings):
GoogleX Labs: http://www.pocket-lint.com/news/126681-google-x-explained-what-s-reallygoing-on-at-google-s-secret-lab
Ted Talks videos on technology: https://www.ted.com/topics/technology
MIT Technology Review: http://www.technologyreview.com/
20
CNET’s Next Big Thing: https://www.cnet.com/next-big-thing/
Be sure to connect the technology with the operations of the subsidiary. Be sure to assess the impact
on the subsidiary.
Deliverable: Provide an interim Environmental Scanning report which summarizes of your findings re:
addressing the opportunities and threats to the subsidiary, identifying disruptive technologies and
assessing their impacts to the subsidiary. (An interim report will be consolidated to a final deliverable in
a later step.) Minimum length = 400 words.
2) Research Innovation and Innovation Cycles
In this step, you are to gain an understanding of concept of innovation, technological innovation and the
generic innovation cycle.
This source provides one perspective of innovation and technological innovation:
https://books.google.com/books?id=qaqeAwAAQBAJ&printsec=frontcover&dq=innovation+definition&
hl=en&sa=X&ei=yENFVai3HMOfNsucgIAD&ved=0CFkQ6AEwBw#v=onepage&q=innovation%20definition
&f=false
Research the different innovation cycles that are out there. One can be found at:
https://hitconsultant.net/2012/11/27/6-steps-of-healthcare-innovation-with-naomi-fried/
One that uses a turbine metaphor (Pg. 15 and 19) can be found at:
https://books.google.com/books?id=3VRs0vB25PoC&pg=PA7&dq=innovation+lifecycle&hl=en&sa=X&ei
=5UVFVZKBCpPWgwSt3oGAAw&ved=0CEcQ6AEwBw#v=onepage&q=innovation%20lifecycle&f=false
There are others you can research.
Deliverable: Provide a report that compares and contrast the different generic innovation cycles.
Include a table that summarizes the attributes of these innovation cycles. Minimum length = 400 words.
3) Operationalize the Innovation Cycle
Based on one or more of the innovation cycles identified in the previous step, create a detailed process
for innovation that is customized for the subsidiary you selected. Discuss how it will change the culture
of the subsidiary to be more oriented to innovation and creativity.
You might want to review this reference on the role of organizational climate on innovation
implementation (Pg. 68):
https://books.google.com/books?id=JRf7TxYef70C&pg=PA68&dq=innovation+implementation&hl=en&s
a=X&ei=YkdFVaK2DsaqNqeRgZgF&ved=0CEoQ6AEwBw#v=onepage&q=innovation%20implementation&
f=false
Deliverable: Prepare an interim “Innovation Corporate Action Plan” that addresses the findings from this
step. Minimum 400 words. Include at least 3 references.
21
4) Develop a Migration Strategy
Research way on how to implement this new innovation process in the subsidiary. Discuss any change
management issues.
Here are articles that may be helpful:
http://georgecouros.ca/blog/archives/3890
https://www.ccl.org/blog/7-strategies-for-developing-a-more-innovative-organization/
https://www.mckinsey.com/business-functions/strategy-and-corporate-finance/ourinsights/leadership-and-innovation
https://www.strategy-business.com/article/00255?gko=9d35b
Deliverable: Migration plan. Minimum: 400 words. Include at least 3 references.
5) Prepare an Executive Presentation
Compile all of the key findings of previous steps and prepare a narrated PowerPoint presentation. It
must be relevant to the subsidiary. It should address as a minimum:
• Future opportunities and threats
• Relevant disruptive technologies
• Proposed innovation cycle (high-level)
• Proposed innovation process
• Migration strategy
• Conclusion
The presentation should consist of 10-15 slides. It should include audio narration (directions are
found at: https://support.office.com/en-au/article/Add-narration-to-a-presentation-0b9502c6-5f6c40ae-b1e7-e47d8741161c). The narration should also be captured in the slide notes.
4. Deliverables
1) Environmental scanning report
2) Innovation Cycle matrix or research document
3) Innovation corporate action plan
4) Migration plan
5) Final presentation
Except for the presentation, combine all of the files into one Word document. Provide an abstract,
introduction, table of contents and conclusion in this one document.
Title your files using this protocol: LastName_FirstName_I-3_AssignmentName_Date.
In lieu of submitting the presentation, you may provide a link to your presentation file.
22
5. Rubrics
Criteria Weight
(%)
Score
Evaluate threats and opportunities and relevant technologies as the
basis for environmental scanning.
20
Illustrate an understanding of innovation concepts and cycles 20
Assess operational processes that facilitates the initiation and
implementation of innovations in organizations
30
Create a migration strategy in transforming an enterprise architecture 20
Exhibit communication skills 10
Total 100
Additional References
Brabham, D. 2013. Crowdsourcing (MIT Press Essential Knowledge). Boston: MIT Press.
Linkner, J. (June 16, 2011). 7 Steps to a culture of innovation. Retrieved from
http://www.inc.com/articles/201106/josh-linkner-7-steps-to-a-culture-of-innovation.html
23
Group Projects
24
Group Project G-1
1. Title
Infrastructure Modernization Review
2. Introduction
The Chief Technology Officer (CTO) for Largo Corporation is responsible for information technology (IT)
that supports the company goals. More specifically, the CTO plays a key role in defining the strategy and
approach for effectively applying information technology to enable the goals and objectives of the
organization to be carried out.
Largo Corporation is a multinational conglomerate corporation that serves a broad range of clients and
their needs. Think in terms of a large company like General Electric which is involved in a wide range of
businesses. Largo Corporation is a high energy organization in an extremely competitive environment
that strives for high quality and timely delivery of products and services to its clients. Ms. Tara Johnson,
the Chief Executive Officer (CEO), is a driven leader who has high expectations on her managers and
employees.
Ms. Johnson has been disappointed with the poor company performance last quarter. Her personal
opinion is that the organization is underutilizing information technology (IT). She feels that there are
state-of-the-art and emerging technologies that can be applied to the company that can immediately
address current user issues and improve the efficiency and effectiveness of its operations.
She asked the CTO to form an IT modernization team to conduct an analysis to determine where the
company’s current IT infrastructure is misaligned with the company’s business needs and to identify
recommendations. In addition, the team must prepare a presentation describing a proposal to
modernize the IT infrastructure and report to the CEO and other corporate executives.
It is common for organizations to have modernization projects. Reasons for these projects include a
new set of business requirements being introduced, the emergence of new technologies that can be
leveraged and past political and budget issues that have slowed down the infusion of technology into
the organization over time.
You will learn about infrastructure components such as hardware; software; and networks and
telecommunications. You will also learn how to evaluate these technologies to meet business
requirements with consideration to the corporate mission and culture. In addition you will be
developing communication, critical thinking, and leadership skills.
Understanding system capabilities provided by the infrastructure components and the application of this
knowledge to enable an organization’s strategic goals and objectives to encompass core knowledge,
skills, and abilities are a knowledge base that IT personnel are expected to possess. Effective IT
professionals are expected to be up-to-date on trends in technology, current IT innovations, and which
technologies will provide a competitive advantage for an organization. Most importantly, IT
professionals must be able to communicate effectively (orally and written) to executive level
management in a non-jargon, executive level manner that convincingly justifies the need to invest in IT
25
improvements and modernization. This learning demonstration is designed to strengthen these
essential knowledge, skills, and abilities needed by IT professionals.
3. Steps to Completion
Your instructor will form the teams. Each member is expected to contribute to the team agreement
which documents the members’ contact information and sets goals and expectations for the team.
1) Review the Setting
Largo Corporation is a major multinational conglomerate corporation which specializes in a wide array
of products and services. These products and services include healthcare, finance, retail, government
services, and many more. The annual revenue is about $750 million and it has about 1,000 employees.
The parent company is located in Largo, Maryland and its subsidiaries are headquartered throughout
the United States.
The mission of the corporation is to bring the best products and services to people and businesses
throughout the world so they can then realize their full potential.
The corporate vision guides every aspect of their business to achieve sustainable, quality growth:
• Productivity: Be a highly effective, lean and fast-moving organization.
• People: Be a great place to work where people are inspired to achieve their maximum potential.
• Partners: Nurture a winning network of customers and suppliers, together we create mutual,
enduring value.
• Responsible: Be a responsible citizen that makes a difference through ethical behavior.
• Revenue: Maximize long-term return while being mindful of our overall responsibilities.
The company’s culture is reflected in their corporate values:
• Leadership: Courage to shape a better future.
• Collaboration: Leverage collective intelligence.
• Accountability: Own up to your responsibility.
• Passion: Committed to excellence.
• Diversity: Provide new perspectives into our business.
• Quality: We will want quality as part of our brand.
The corporation consists of the parent company and the following subsidiaries:
• Healthcare – Suburban Independent Clinic, Inc. (medical services)
• Finance – Largo Capital (financial services)
• Retail – Rustic Americana (arts and crafts), Super-Mart (office products)
• Government Services – Government Security Consultants (information security)
26
• Automotive – New Breed (electric cars)
• Systems Integration – Solutions Delivery, Inc. (communications)
• Media Design – Largo Media (website and app design)
The organization is headed by CEO Tara Johnson who completed her Master’s degree at UMUC and
eager to make worthwhile improvements to the corporation. She rose through the ranks of Largo
Corporation starting with systems integration, then retail and her last position before becoming CEO
was in finance.
The corporation is in a highly competitive environment so the CEO wants savvy employees at many
levels to make wise judgments and take an aggressive approach and deliver results towards improving
the bottom line yet maintaining corporate social responsibility.
2) Gauging the Current Situation
One area CEO Tara Johnson is most concerned about is the IT infrastructure of her company. Some of
the subsidiaries of the corporation underperformed last quarter and she has the opinion that existing IT
infrastructure contributed to the decline.
Ms. Johnson set up interviews with various stakeholders both internal and external to the corporation to
gain some insight into the IT concerns. They were asked “What is the most problematic issue facing you
with regard to information technology.” These were the responses:
“It was difficult to implement new government regulatory requirements due to outdated
software systems.” (Chief Counsel, Largo Corporation)
“Our computer workload varies greatly day to day and sometimes our network just cannot keep
up the demand.” (Retail Operations Manager, Rustic Americana)
“The organization was not able to properly analyze its data and get the information to make
quality decisions quickly.” (Department Head, Largo Capital)
“The networks are often slow and unreliable. It was built in the 1980’s!” (Web Designer, Largo
Media)
“We need a more secure and less expensive way to record transactions involving the purchase
of IT equipment. The current approach requires a lot of verifications!” (Purchasing Manager,
Rustic Americana)
“It seems that our people who do field work could use IT to improve their operations.”
(Communications Field Manager, Solutions Delivery, Inc.)
“Our doctors needs more insight on diagnosing complex medical problems. They have to dig
into research journals and contact experts. This takes an inordinate amount of time.
27
Information is delivered in long written reports. There must be a better way!” (Head of
Physicians, Suburban Independent Clinic)
“Each business unit could not exchange information easily with another business unit. For
example, the financial personnel could not send budget information to the operation people
without a lengthy period to convert and massage the data”. (Financial analyst, Largo Capital)
“I am concerned that we do not encrypt our corporate wireless networks.” (Security specialist,
Government Security Consultants)
“Our employees are creating gigabytes and gigabytes of data. Our hard disks are running out of
space!” (Call Center Manager, Rustic Americana)
“We are getting virus and other malware all the time. What should we do?” (Operations
analyst, Super-Mart)
“I am worried about the possibility of privacy intrusions in our medical operations.” (Doctor,
Suburban Independent Clinic)
“Employees want to bring in their own personal devices but the network people won’t let them
connect with our systems.” (Branch Manager, New Breed)
“We business managers think that the IT personnel often fail to listen and understand our
specific needs, always want to use cutting edge but unproven tools, do not ask the right
questions and lack vision.” (Department Head, Largo Corporation)
“As an IT professional, it seems to me that business people are unclear about their needs,
constantly changing their requirements and do not understand the cost and time issues
associated with technology implementation.” (Systems Developer, Largo Corporation)
“Many of our younger employees see security as an interference and actually know how to
successfully work around security protocols.” (Operational manager, Super-Mart)
“When we call the Helpdesk for support, we never know how soon they will assist us. We have
to do our jobs and have no idea what the priority is and when our issue will be addressed.”
(Administrative Assistant, Largo Corporation)
“Developers do not talk to us production types. They throw their applications over the transom
and leave us to fix them!” (COO, SIC)
3) Analyze the Issues
28
Your work begins now. As the part of the IT modernization team, this step requires you to study and
analyze these IT issues. As a first step you can group these issues into different categories such as
software, hardware, networks/telecommunications, management issues, and others.
In analyzing each issue, consider asking these questions:
• Do I understand the meaning and nature of the issue?
• Should we care about this issue?
• What does literature say about this issue?
• Who is affected by the issue? How so?
• Which issues are most important? Least important?
• How does this issue relate to corporate strategy and goals?
• Why do you think this issue occurred?
Do not jump the gun and identify solutions. That step comes later.
Deliverable: Prepare a narrative and a summary table that would capture the results of your analysis in
this step. Minimum length = 600 words. Be sure to state your assumptions.
4) Research Technologies and Technology Trends
Investigate and evaluate the current and emerging technologies that have the potential of addressing
the identified issues. Review your readings, library resources and other peer-reviewed references.
As part of this investigation, determine the relevance of the following technology trends: cloud
computing, virtualization, mobile computing, Big Data, artificial intelligence, block chain and other
contemporary IT cross-functional approaches to the issues at hand.
Also, discuss management solutions that are closely related to the technology implementations (such as
BYOD) that can address the issues identified.
Deliverable: Provide a technical briefing that examines different relevant technologies and technology
trends and include a short description of each. Also, explain why these technologies are applicable to
Largo Corporation. In addition, discuss technology-related management solutions. Minimum length =
1,000 words.
5) Communicate the Overall Findings and Recommendations
Provide a presentation that addresses a set of recommendations on the technologies and trends needed
to address the current situation. A suggested agenda is as follows:
• Purpose of the Briefing
• Description of the Overall Environment
• Analysis of the Issues
29
• Relevant Technologies that Address the Issues including Rationale
• Relevant Trends that Potentially Address the Issues including Rationale
• Technology-based Management Solutions that Address the Issues
• Overall Recommendations
• Conclusions
The audience consists of the CEO and executives representing all of Largo Corporation subsidiaries. The
presentation should consist of 15-20 slides. It should include audio narration (directions are found at:
https://support.office.com/en-au/article/Add-narration-to-a-presentation-0b9502c6-5f6c-40ae-b1e7-
e47d8741161c). The narration should also be captured in the slide notes.
Prepare a peer evaluation report.
4. Deliverables
1) Issue analysis table (from Step 3)
2) Technology/Management briefing (from Step 4)
3) Final presentation (from Step 5)
Except for the presentation, combine all of the files into one Word document. Provide an abstract,
introduction, table of contents and conclusion in this one document.
Title your files using this protocol: GroupNumber_G-1_AssignmentName_Date.
In lieu of submitting the presentation, the team leader may provide a link to the presentation file.
NOTE: At the end of the project, each member of the team should email a completed Peer Evaluation
form to your instructor.
5. Rubrics
Criteria Weight Score
Analyze technical and non-technical issues that are evident in a given IT
infrastructure
20
Identify the appropriate technology solutions to address identified issues 50
Identify the appropriate management solutions to address identified
issues
20
Exhibit communication skills 10
Total 100
30
Group Project G-2
1. Title
IT Security Risk Assessment
2. Introduction
You are employed with Government Security Consultants, a subsidiary of Largo Corporation. As a
member of IT security consultant team, one of your responsibilities is to ensure the security of assets as
well as provide a secure environment for customers, partners and employees. You and the team play a
key role in defining, implementing and maintaining the IT security strategy in organizations.
A government agency called the Bureau of Research and Intelligence (BRI) is tasked with gathering and
analyzing information to support U.S. diplomats.
In a series of New York Times articles, BRI was exposed as being the victim of several security breaches.
As a follow up, the United States Government Accountability Office (GAO) conducted a comprehensive
review of the agency’s information security controls and identified numerous issues.
The head of the agency has contracted your company to conduct an IT security risk assessment on its
operations. This risk assessment was determined to be necessary to address security gaps in the
agency’s critical operational areas and to determine actions to close those gaps. It is also meant to
ensure that the agency invests time and money in the right areas and does not waste resources. After
conducting the assessment, you are to develop a final report that summarizes the findings and provides
a set of recommendations. You are to convince the agency to implement your recommendations.
This learning activity focuses on IT security which is an overarching concern that involves practically all
facets of an organization’s activities. You will learn about the key steps of preparing for and conducting
a security risk assessment and how to present the findings to leaders and convince them into taking
appropriate action.
Understanding security capabilities is basic to the core knowledge, skills, and abilities that IT personnel
are expected to possess. Information security is a significant concern among every organization and it
may spell success or failure of its mission. Effective IT professionals are expected to be up-to-date on
trends in IT security, current threats and vulnerabilities, state-of-the-art security safeguards, and
security policies and procedures. IT professionals must be able to communicate effectively (oral and
written) to executive level management in a non-jargon, executive level manner that convincingly
justifies the need to invest in IT security improvements. This learning demonstration is designed to
strengthen these essential knowledge, skills, and abilities needed by IT professionals.
31
3. Steps to Completion
Your instructor will form the teams. Each member is expected to contribute to the team agreement
which documents the members’ contact information and sets goals and expectations for the team.
1) Review the Setting and Situation
The primary mission of the Bureau of Research and Intelligence (BRI) is to provide multiple-source
intelligence to American diplomats. It must ensure that intelligence activities are consistent with U.S.
foreign policy and kept totally confidential. BRI has intelligence analysts who understand U.S. foreign
policy concerns as well as the type of information needed by diplomats.
The agency is in a dynamic environment in which events affecting foreign policy occur every day. Also,
technology is rapidly changing and therefore new types of security opportunities and threats are
emerging which may impact the agency.
Due to Congressional budget restrictions, BRI is forced to be selective in the type of security measures
that it will implement. Prioritization of proposed security programs and controls based on a sound risk
assessment procedure is necessary for this environment.
The following incidents involving BRI’s systems occurred and reported in the New York Times and other
media outlets:
• BRI’s network had been compromised by nation-state-sponsored attackers and that attacks are
still continuing. It is believed that the attackers accessed the intelligence data used to support
U.S. diplomats.
• The chief of the bureau used his personal e-mail system for both official business purposes and
for his own individual use.
• A software defect in BRI’s human resource system – a web application – improperly allowed
users to view the personal information of all BRI employees including social security numbers,
birthdates, addresses, and bank account numbers (for direct deposit of their paychecks). After
the breach, evidence was accidently destroyed so there was no determination of the cause of
the incident or of its attackers.
• A teleworker brought home a laptop containing classified intelligence information. It was stolen
during a burglary and never recovered.
• A disgruntled employee of a contractor for BRI disclosed classified documents through the
media. He provided the media with, among other things, confidential correspondence between
U.S. diplomats and the President that were very revealing.
32
• Malware had infected all of the computers in several foreign embassies causing public
embarrassment, security risks for personnel and financial losses to individuals, businesses and
government agencies including foreign entities.
These reports prompted the U.S. Government Accountability Office to conduct a comprehensive review
of BRI’s information security posture. Using standards and guidance provided by the National Institute
of Standards and Technology and other parties, they had the following findings:
Identification and Authentication Controls
• Controls over the length of passwords for certain network infrastructure devices were set to less
than eight characters.
• User account passwords had no expiration dates.
• Passwords are the sole means for authentication.
Authorization Controls
• BRI allowed users to have excessive privileges to the intelligence databases. Specifically, BRI did
not appropriately limit the ability of users to enter commands using the user interface. As a
result, users could access or change the intelligence data.
• BRI did not appropriately configure Oracle databases running on a server that supported
multiple applications. The agency configured multiple databases operating on a server to run
under one account. As a result, any administrator with access to the account would have access
to all of these databases; potentially exceeding his/her job duties.
• At least twenty user accounts were active on an application’s database, although they had been
requested for removal in BRI’s access request and approval system.
Data Security
• BRI does not use any type of data encryption for data-at-rest but protects data-in-transit using
VPN.
• A division data manager can independently control all key aspects of the processing of
confidential data collected through intelligence activities.
• One employee was able to derive classified information by “aggregating” unclassified databases.
• Hackers infiltrated transactional data located in a single repository and went ahead and
corrupted it.
33
System Security
• Wireless systems use the Wired Equivalent Privacy (WEP) standard for ensuring secure
transmission of data.
• The agency permitted the “Bring Your Own Device” (BYOD) concept and therefore users can
utilize their personal mobile devices to connect to the agency network freely.
• In the event of a network failure due to hacking, the data center manager has his recovery plan
but has not shared it with anyone in or out of the center. He was not aware of any requirement
to report incidents outside of the agency.
• There has never been any testing of the security controls in the agency.
• Processes for the servers have not been documented, but in the minds of the system managers.
• Patching of key databases and system components has not been a priority. Patching systems
have either been late or not performed at all. Managers explained that it takes time and effort
to test patches on its applications.
• Scanning devices connected to the network for possible security vulnerabilities are done only
when the devices are returned to inventory for future use.
• System developers involved with financial systems are allowed to develop code and access
production code.
Physical Security
• An unauthorized personnel was observed “tailgating” or closely following an official employee
while entering a secure data center.
• The monthly review process at a data center failed to identify a BI employee who had separated
from BRI and did not result in the removal of her access privileges. She was still able to access
restricted areas for at least three months after her separation.
End User Security
• Users even in restricted areas are allowed to use social media such as Facebook. The argument
used is that is part of the public outreach efforts of the agency.
• Users receive a 5-minute briefing on security as part of their orientation session that occurs
typically on their first day of work. There is no other mention of security during the course of
employment.
• Users are allowed to use public clouds such as Dropbox, Box, and Google Drive to store their
data.
34
• BRI has not performed continual background investigations on employees who operate its
intelligence applications (one investigation is conducted upon initial employment).
• There is no policy regarding the handling of classified information.
An internal audit report indicated that the organization needed several security programs including a
security awareness and training program, a privacy protection program and a business
continuity/disaster recovery programs. These programs will need special attention.
2) Examine Background Resources
This learning demonstration focuses on the National Institute of Standards and Technology’s (NIST)
“Guide for Conducting Risk Assessments”
(http://csrc.nist.gov/publications/nistpubs/800-30-rev1/sp800_30_r1.pdf). See Pg. 23 to view the
description of the risk management process.
Throughout this learning activity, feel free to use other references such as:
Other NIST publications (http://csrc.nist.gov/publications/PubsSPs.html),
SANS Reading Room (http://www.sans.org/reading-room/),
US-CERT (https://www.us-cert.gov/security-publications),
CSO Magazine (http://www.csoonline.com/),
Information Security Magazine (http://www.infosecurity-magazine.com/white-papers/),
Homeland Security News Wire (http://www.homelandsecuritynewswire.com/topics/cybersecurity)
Other useful references on security risk management include:
https://books.google.com/books?id=cW1ytnWjObYC&printsec=frontcover&source=gbs_ge_summary_r
&cad=0#v=onepage&q&f=false
https://books.google.com/books?id=FJFCrP8vVZcC&printsec=frontcover&source=gbs_ge_summary_r&c
ad=0#v=onepage&q&f=false
3) Prepare the Risk Assessment Plan
Using the NIST report as your guide, address the following items:
• Purpose of the assessment,
• Scope of the assessment,
• Assumptions and constraints, and
• Selected risk model and analytical approach to be used.
Document your above analysis in the “Interim Risk Assessment Planning Report.” (An interim report will
be consolidated to a final deliverable in a later step.)
35
All interim reports should be at least 500 words long and include at least five references for each report.
These reports will eventually be presented to management for their review.
4) Conduct the Assessment
Again, use the NIST report to address the following:
1) Identify threat sources and events
2) Identify vulnerabilities and predisposing conditions
3) Determine likelihood of occurrence
4) Determine magnitude of impact
5) Determine risk
You are free to make assumptions but be sure to state them in your findings.
In determining risk, include the assessment tables reflect BRI’s risk levels. Refer to Appendix I. on risk
determination in Special Publication 800-30.
Document your analysis from this step in the “Interim Risk Assessment Findings Report.” Be sure to
include the final risk evaluations in this report.
5) Identify Needed Controls and Programs
Research and specify security controls needed to close the security gaps in BRI.
Also, be sure to include a description of the following programs for securing BRI:
• Security Awareness and Training Program (i.e., communications to employees regarding
security)
• Privacy Protection Program
• Business Continuity/Disaster Recovery Program
You should justify the need for the agency to invest in your recommendations.
Document your findings and recommendations from this step in the “Interim Security
Recommendations Report.”
6) Communicate the Overall Findings and Recommendations
Integrate of your earlier interim reports into a final management report. Be sure to address:
• Summary of the Current Security Situation at BRI (from Step 1)
• Risk Assessment Methodology (from Step 2)
• Risk Assessment Plan (from Step 3)
• Risk Assessment Findings (from Step 4)
36
• Security Recommendations Report (from Step 5)
• Conclusions
Also provide a presentation to management. The presentation should consist of 15-20 slides. It should
include audio narration (directions are found at: https://support.office.com/en-au/article/Addnarration-to-a-presentation-0b9502c6-5f6c-40ae-b1e7-e47d8741161c). The narration should also be
captured in the slide notes.
Prepare a peer evaluation report.
4. Deliverables
• Final Management report (as described in Step 6)
• PowerPoint Presentation
Except for the presentation, combine all of the files into one Word document. Provide an abstract,
introduction, table of contents and conclusion in this one document.
Title your files using this protocol: GroupNumber_G-2_AssignmentName_Date.
In lieu of submitting the presentation, the team leader may provide a link to the presentation file.
NOTE: At the end of the project, each member of the team should email a completed Peer Evaluation
form to your instructor.
5. Rubrics
Criteria Weight Score
Identify threats and vulnerabilities associated with information systems
and assess their risks
30
Formulate the appropriate security controls to address the identified
threats and vulnerabilities
30
Communicate to employees an awareness of security issues related to IT
systems
10
Evaluate organizational information systems to insure they protect the
privacy of users and of customers
10
Determine requirements for business continuity/disaster recovery plans
and backup procedures
10
Exhibit communication skills 10
Total 100
37
Additional References
Ross, R. (2014). Security and privacy controls for federal information systems and organizations. NIST
Special Publication 800-53. Retrieved from http://dx.doi.org/10.6028/NIST.SP.800-53r4
Swanson, M., Wohl, A., Pope, L., Grance, T., Hash, J. & Thomas, R. (2002). Contingency planning guide
for information technology systems. NIST Special Publication 800-34. Retrieved from
http://ithandbook.ffiec.gov/media/22151/ex_nist_sp_800_34.pdf
Wilson, M. & Hash, J. (2003). Building an information technology security awareness and training
program. NIST Special Publication 800-50. Retrieved from
http://csrc.nist.gov/publications/nistpubs/800-50/NIST-SP800-50.pdf
38
Group Project G-3
1. Title
Health Information Technology Architecture
2. Introduction
Largo Corporation has recently acquired Suburban Independent Clinic, Inc. (SIC) which serves the
general outpatient medical needs of a suburb just outside of Washington, D.C. It competes directly with
CVS Minute Clinic and Urgent Care Center. The corporation appointed you as the chief information
officer (CIO) of the clinic in charge of managing clinical and administrative information, technologies and
systems.
The clinic is feeling the pressure in many respects – cost, quality of care, access, and efficiency. Disease
and personal injuries are on the rise, requirements for efficient and effective care delivery are
increasing, and healthcare costs have climbed over time.
Legislation such as the Affordable Care Act has called for the greater adoption of health information
technology to improve access, delivery, efficiency and quality of health care serves and treatments while
reducing costs and the occurrence of medical errors. This project explores the development and use of
information technology IT since it has emerged as a powerful enabler in helping to achieve multiple
goals and objectives across the entire U.S. healthcare system.
As the CIO you realize the value and importance of applying IT and have been asked to analyze the
issues faced by the clinic and develop a new IT architecture for the facility.
You will benefit from this project in that it will develop your knowledge of information technology in the
context of the health care field. So welcome to the world of health information technology and let’s
begin this journey step-by-step.
3. Steps to Completion
Your instructor will form the teams. Each member is expected to contribute to the team agreement
which documents the members’ contact information and sets goals and expectations for the team.
1) Understand the Setting
The mission statement of Suburban Independent Clinic is as follows:
1. Provide high quality medical care to the patient regardless of race, ethnicity, and gender.
2. Optimize visit experience, communication standards and patient understanding.
3. Treat patients with respect.
4. Maintain patient confidentiality and security.
5. Provide a pleasing working environment for employees.
39
6. Follow established policies and procedures for clinics such as HIPAA.
Besides yourself, employees include:
• Clinic Director
• Attending physicians (general practitioners)
• Nurses
• Office manager [designated as the Health Information Management (HIM) Manager]
• Receptionist/Interpreter
A survey was conducted involving the patients and specific employees of SIC. Here is a representative
sample of their feedback:
Patient
• I can only make appointments by phone. SIC, you need to move to the 21st century!
• The only way I can view my medical record is by being physically in the office.
• Boy, it takes a really long time for the office people to find my medical records. I notice that they
keep them in paper files. Once they gave the doctor the wrong record for me because I had the
same name as another patient.
• I once saw an employee leave my medical records out in the open where anyone can view it!
• I have to complete all forms by hand. What a pain!
• Drug costs are skyrocketing. We need to look if pharmaceutical companies are ripping us off!
• My pharmacist once told me that the prescription from the doctor was difficult to read. She had
to call the doctor’s office to find out what medication was being prescribed.
• I often forget what the doctor told me after my examination especially when he gives a lot of
instructions.
• I had a drug-drug interaction that could have been prevented. I am suing SIC!
• I have a difficult time getting to the office. No one will take me and the cost of a taxi is
expensive.
• I like the fact that the receptionist is bilingual but sometimes she is too busy and cannot
interpret for me.
• I don’t like searching for information and reading a lot of reports. I wish there was a way to get
the information I want quickly and accurately as if a doctor or nurse was talking to me.
40
Physician
• I cannot read the handwritten charts from Dr. Smith because of his lousy penmanship. Some
comments he includes are scribbled in the margins.
• I like to identify trends and patterns among my patients (is there an epidemic of a particular
virus?) but it is too much of a manual process to compile and compare all of the records. I also
like to explore trends among all clinics in the region and in the country.
• It takes a long time to get patient records from the filing cabinet. It is sometimes misfiled or
even missing!
• I wish I could better communicate with my patients beyond an office conversation.
• I want to start a wellness program but printing and mailing costs makes it prohibitive.
• I wish I could see the patient’s medical history from birth to the present particularly when the
patient has changed doctors.
• I have a difficult time managing my certifications. They are all lying in my office drawer or
hanging in frames.
• I like spending time with patients and teaching but I hate the paperwork and administration
issues I face every day!
• We need more insight on diagnosing complex medical problems. We have to dig into research
journals and contact experts. This takes an inordinate amount of time. Information is delivered
in long written reports. There must be a better way!
Nurse
• Often medical supplies were low and had to be ordered them by phone at the last minute.
• Sometimes there is an inadequate staffing of nurses and I have to work a double shift. It’s just
not fair!
• Occasionally we have to repeat tests because we cannot find the patient’s data.
• I don’t have the time to take training sessions I need during regular office hours.
• It takes a while to contact immunization registries by phone.
• I am spend less and less time on patient care and more time with bookkeeping.
41
Office Manager / HIM Manager
• The facility is running out of space due to the frequent addition of file cabinets to hold the
growing patient data. It is expensive to buy these cabinets and we are losing space that we
normally use for patient care.
• Documentation is inadequate when corporate auditor want to examine records for cost and
compliance reviews.
• Once we lose medical records they were gone forever.
• Health insurance claims are handled manually and subject to errors. And when there is changes
in the rules, we learn about it much too late and some employees are not informed of the
change.
• We have a frequent cash flow problems because we tend to send bills late. We should ask for
payments on the spot!
• Please, I don’t want to use computer technology since it will increase costs tremendously. I
don’t believe those computer systems vendors – they are just out to make a buck.
• I am overworked and underpaid! I would like to start a union of clinic office managers!
• Archived medical records are stored in a warehouse. If they need to be retrieved they need to
faxed, scanned or mail which is a time consuming process when it could be a life or death
situation.
• We keep all of our equipment purchasing data in one server and I am worried about someone
coming in and corrupting it. In addition there are many verifications needed to ensure data is
accurate. We need to hire a lot of trusted third parties to do this. I wish life was more simple!
2) Analyze the Issues
Your work begins now. As a first step you are to organize these issues into logical categories and
prioritize them.
In analyzing each issue, think about these questions:
• Do I understand the meaning and nature of the issue?
• Should we care about this issue?
• What does literature say about this issue?
• Who is affected by the issue? How so?
• Which issues are most important? Least important?
• How does this issue relate to corporate strategy and goals?
Do not jump the gun and start identifying solutions now. That step comes later.
42
Deliverable: Prepare a narrative and a summary table that would capture the results of your issue
analysis in this step. The table should prioritize the issues in the context of SIC and Largo Corporation.
Minimum length = 600 words. Be sure to state your assumptions.
3) Research Technologies and Technology Trends
Investigate and evaluate the current and emerging technologies that have the potential of addressing
the identified issues. Review your readings, library resources and other peer-reviewed references.
Evaluate the relevance of the following technology trends and approaches:
• Electronic health records (EHR)
• Computerized provider order entry (CPOE)
• Bar code medication administration (BCMA)
• Medication management system
• Robotics/Workstations on wheels (WOW)
• Mobile technologies and apps
• Internet-based applications
• Enterprise Resource Planning
• Cloud computing
• Big Data technologies
• Collaborative technologies
• Decision support systems
You are not limited to the above list in your analysis.
Review and evaluate the relevancy of IT trends and approaches to the current situation. Review your
readings, library resources and other peer-reviewed references.
Deliverable: Provide a technical briefing that examines different technologies and technology trends
relevant to SIC’s issues include a short description of each. Also, explain why these technologies are
applicable to SIC’s challenges. Minimum length = 1,000 words.
4) Prepare a migration strategy
Moving from the “as-is” to the “to-be” state can very challenging. Review techniques for migrating an
organization to a new set of technologies and processes. Keep in mind change management strategies.
Deliverable: Outline a plan that addresses how the organization will move to its new architecture.
5) Communicate the Overall Findings and Recommendations
Provide a presentation that addresses a set of recommendations on the technologies and trends needed
to address the current situation. A suggested agenda is as follows:
43
• Purpose of the Briefing
• Description of the Overall Environment
• Analysis of the Issues
• Relevant Technologies that Address the Issues including Rationale
• Overall Recommendations
• Proposed Migration Strategy
• Conclusions
The audience consists of the CEO and executives representing Largo Corporation and SIC.
The presentation should consist of 15-20 slides. It should include audio narration (directions are found
at: https://support.office.com/en-au/article/Add-narration-to-a-presentation-0b9502c6-5f6c-40aeb1e7-e47d8741161c). The narration should also be captured in the slide notes.
Prepare a peer evaluation report.
4. Deliverables
1) Issue analysis table (from Step 2)
2) Technology briefing (from Step 3)
3) Migration plan (from Step 4)
4) Final presentation (from Step 5)
Except for the presentation, combine all of the files into one Word document. Provide an abstract,
introduction, table of contents and conclusion in this one document.
Title your files using this protocol: GroupNumber_G-3_AssignmentName_Date.
In lieu of submitting the presentation, the team leader may provide a link to the presentation file.
NOTE: At the end of the project, each member of the team should email a completed Peer Evaluation
form to your instructor.
5. Rubrics
Criteria Weight Score
Analyze technical issues that are evident in a clinical environment 20
Identify the appropriate technology solutions to address identified issues 40
Describe a viable migration plan 20
Exhibit communication skills 20
Total 100