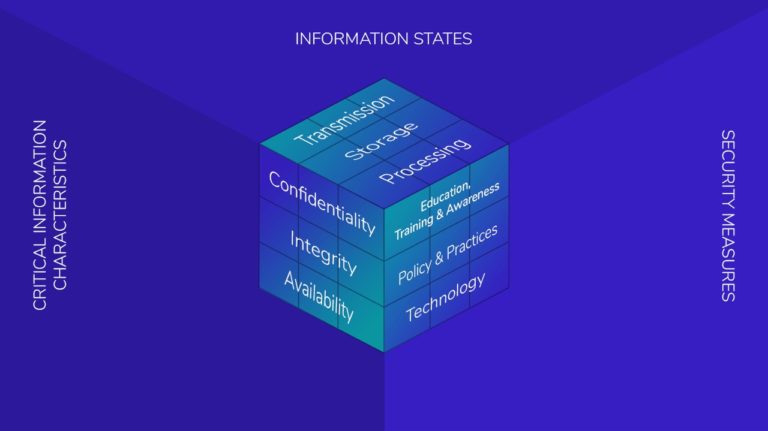
INTRODUCTION TO CYBERSECURTY
Assuming you are planning to work in the Northern Virginia area after graduation. There are some resources to prepare you for this. This week’s discussion is about planning for your future. 1. 1. Review the 2022 Labor Market: https://www.nvcc.edu/osi/labor-market/_docs/23-001-IndexSurveyReport22-final-web.pdfLinks to an external site. 2. 2. Download and read/review the Greater Washington Technology Workforce Needs Assessment report. … Read more